Docker远程访问安全问题与TLS配置并通过IDEA连接
Docker远程访问安全问题与TLS配置并通过IDEA连接
在使用Docker的时候,会用到远程访问这个功能。如果不配置Docker远程控制的TLS,任何人都可以通过远程控制端口控制Docker,有极大的安全隐患,开启个十几分钟,就有可能被端口扫描到从而被劫持。
TLS通过加密传输数据并进行身份验证来增强通信安全性。
新建一个Shell脚本
nano docker-tls.sh复制粘贴以下脚本内容
#!/bin/bash
set -e
CERT_DIR="cert/docker"
mkdir -p "$CERT_DIR"
if [ -z "$1" ]; then
echo "请输入主机名作为参数"
exit 1
fi
HOST="$1"
# 生成证书和密钥文件
openssl genrsa -aes256 -out "$CERT_DIR/ca-key.pem" 4096
openssl req -new -x509 -days 3650 -key "$CERT_DIR/ca-key.pem" -sha256 -out "$CERT_DIR/ca.pem"
openssl genrsa -out "$CERT_DIR/server-key.pem" 4096
openssl req -subj "/CN=$HOST" -sha256 -new -key "$CERT_DIR/server-key.pem" -out "$CERT_DIR/server.csr"
echo subjectAltName = DNS:$HOST,IP:0.0.0.0 > "$CERT_DIR/extfile.cnf"
openssl x509 -req -days 3650 -sha256 -in "$CERT_DIR/server.csr" -CA "$CERT_DIR/ca.pem" -CAkey "$CERT_DIR/ca-key.pem" -CAcreateserial -out "$CERT_DIR/server-cert.pem" -extfile "$CERT_DIR/extfile.cnf"
openssl genrsa -out "$CERT_DIR/key.pem" 4096
openssl req -subj '/CN=client' -new -key "$CERT_DIR/key.pem" -out "$CERT_DIR/client.csr"
echo extendedKeyUsage = clientAuth > "$CERT_DIR/extfile-client.cnf"
openssl x509 -req -days 3650 -sha256 -in "$CERT_DIR/client.csr" -CA "$CERT_DIR/ca.pem" -CAkey "$CERT_DIR/ca-key.pem" -CAcreateserial -out "$CERT_DIR/cert.pem" -extfile "$CERT_DIR/extfile-client.cnf"
rm -v "$CERT_DIR/client.csr" "$CERT_DIR/server.csr"
chmod -v 0400 "$CERT_DIR/ca-key.pem" "$CERT_DIR/key.pem" "$CERT_DIR/server-key.pem"
chmod -v 0444 "$CERT_DIR/ca.pem" "$CERT_DIR/server-cert.pem" "$CERT_DIR/cert.pem"
echo "证书和密钥文件生成完成"按住Ctrl+O保存,Ctrl+X退出,给予脚本执行权限
chmod +x docker-tls.sh执行脚本
必须传入一个主机名,最好是一个域名,如果没有域名可随意传入一个主机名,连接时使用修改host的方式连接
./docker-tls.sh us.xiny.cc执行过程如下
root@xinycc:~/sh# ./docker-tls.sh us.xiny.cc
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
Enter pass phrase for cert/docker/ca-key.pem:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:cn
State or Province Name (full name) [Some-State]:cn
Locality Name (eg, city) []:cn
Organization Name (eg, company) [Internet Widgits Pty Ltd]:cn
Organizational Unit Name (eg, section) []:cn
Common Name (e.g. server FQDN or YOUR name) []:cn
Email Address []:cn
Certificate request self-signature ok
subject=CN = us.xiny.cc
Enter pass phrase for cert/docker/ca-key.pem:
Certificate request self-signature ok
subject=CN = client
Enter pass phrase for cert/docker/ca-key.pem:
removed 'cert/docker/client.csr'
removed 'cert/docker/server.csr'
mode of 'cert/docker/ca-key.pem' changed from 0600 (rw-------) to 0400 (r--------)
mode of 'cert/docker/key.pem' changed from 0600 (rw-------) to 0400 (r--------)
mode of 'cert/docker/server-key.pem' changed from 0600 (rw-------) to 0400 (r--------)
mode of 'cert/docker/ca.pem' changed from 0644 (rw-r--r--) to 0444 (r--r--r--)
mode of 'cert/docker/server-cert.pem' changed from 0644 (rw-r--r--) to 0444 (r--r--r--)
mode of 'cert/docker/cert.pem' changed from 0644 (rw-r--r--) to 0444 (r--r--r--)
证书和密钥文件生成完成执行过程中要求输入pass phrase,输入一个自定义的密码即可,比如987654321,需要多次输入,保持一致即可。
其中还需要输入国家城市邮箱等信息,随意输入,上图我就全部输入了cn
查看生成的文件
root@xinycc:~# ls cert/docker
ca-key.pem ca.pem ca.srl cert.pem extfile-client.cnf extfile.cnf key.pem server-cert.pem server-key.pem保存ca.pem、cert.pem、key.pem、server-cert.pem、server-key.pem这五个文件,将ca.pem、server-cert.pem、server-key.pem保存至服务器自定义位置。ca.pem、cert.pem、key.pem下载保存到本地电脑。
修改Docker运行配置文件
nano /usr/lib/systemd/system/docker.service将ExecStart=/usr/bin/dockerd 这一行前面添加#号注释,然后在注释行下一行添加以下代码
ExecStart=/usr/bin/dockerd \
--tlsverify --tlscacert=/path/cert/docker/ca.pem \
--tlscert=/path/cert/docker/server-cert.pem \
--tlskey=/path/cert/docker/server-key.pem \
-H tcp://0.0.0.0:2376 -H unix://var/run/docker.sock记得修改path为文件实际所在位置
刷新配置文件并重新启动Docker
systemctl daemon-reload && systemctl restart docker重启后记得打开防火墙的2376端口
保存客户端证书并连接
将ca.pem、cert.pem、key.pem下载保存到电脑,我保存在了D://Software/Docker/cert下
然后打开IDEA,进入到设置-构建运行-Docker中
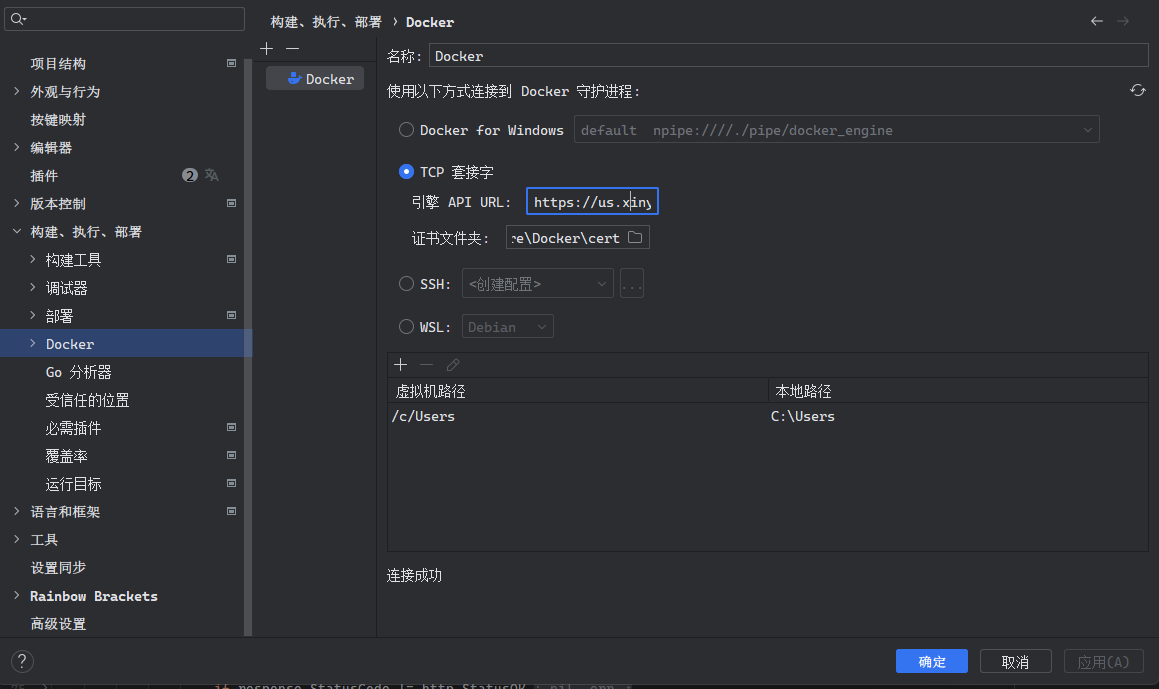
点击+添加docker连接,选择TCP套接字,URL输入https://us.xiny.cc:2376
证书文件夹选择存放证书的文件夹,点击应用,查看是否提示连接成功
本文链接:
/archives/UAo9oL3X
版权声明:
本站所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自
薪萤-博客!
喜欢就支持一下吧
打赏
 微信
微信
 支付宝
支付宝
 微信
微信
 支付宝
支付宝
